Read this Which Cpcon Establishes A Protection Priority Focus On Critical article to find useful information for you, all summarized well by us.
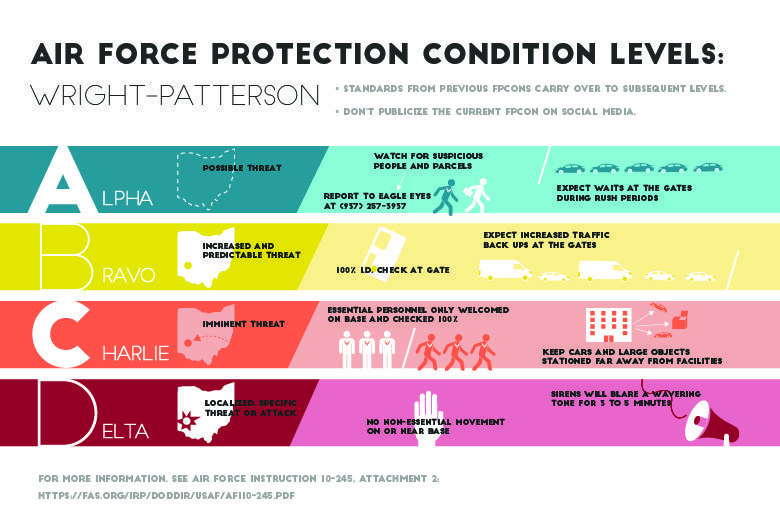
Read this Which Cpcon Establishes A Protection Priority Focus On Critical article to find useful information for you, all summarized well by us.

In the complex and ever-evolving realm of cybersecurity, it is imperative to establish a clear and well-defined protection priority framework to safeguard critical infrastructure and sensitive data. This is where the concept of C-CPCON (Cyber-Critical Infrastructure Protection Coordination Office) comes into play. C-CPCON plays a pivotal role in coordinating and prioritizing cybersecurity efforts across various government agencies and private sector entities.
Among the different C-CPCON initiatives, C-CPCON 4-1 is a particularly notable policy that establishes a protection priority focus on critical infrastructure. This policy outlines a comprehensive framework for identifying, assessing, and prioritizing critical infrastructure assets based on their potential impact on national security or economic well-being. By establishing a clear hierarchy of protection priorities, C-CPCON 4-1 enables stakeholders to allocate resources and implement appropriate cybersecurity measures effectively.
C-CPCON 4-1 defines five levels of protection priorities, ranging from Priority 1 (Highest) to Priority 5 (Lowest). This framework provides a structured approach to classifying critical infrastructure assets based on their criticality and the potential consequences of their disruption. The protection priority levels are assigned based on the following criteria:
By assigning protection priorities, C-CPCON 4-1 helps prioritize cybersecurity investments, improve coordination among stakeholders, and ensure that critical infrastructure assets are adequately protected. The policy also promotes the development and implementation of risk-based cybersecurity measures tailored to the specific needs of each critical infrastructure sector.
The cybersecurity landscape is constantly evolving, presenting new challenges and opportunities. C-CPCON continues to adapt and evolve to address emerging threats and enhance its protection priority framework. Recent trends and developments include:
By staying abreast of these developments, C-CPCON ensures that its protection priority framework remains relevant and effective in the face of evolving threats.
For businesses and organizations seeking to improve their cybersecurity posture and align with C-CPCON 4-1, consider the following expert tips:
By adhering to these tips, organizations can enhance their cybersecurity defenses and align with the protection priority focus established by C-CPCON 4-1.
Here are some frequently asked questions about C-CPCON and its protection priority framework:
C-CPCON 4-1 plays a vital role in safeguarding the nation’s critical infrastructure by establishing a protection priority focus. By understanding the framework and implementing the recommended tips, businesses and organizations can enhance their cybersecurity posture, contribute to national security, and protect sensitive data. As the cybersecurity landscape continues to evolve, C-CPCON remains committed to adapting and innovating to address emerging threats and ensure the protection of critical infrastructure.
Are you interested in learning more about C-CPCON and its protection priority framework? If so, we encourage you to explore additional resources, engage with industry experts, and participate in ongoing discussions to stay informed about cybersecurity best practices and the latest developments in the field.
Which Cpcon Establishes A Protection Priority Focus On Critical has been read by you on our site. Thank you for your visit, and we hope this article is beneficial.